Whether freeing up local disk space, backing up documents, or making files accessible across multiple devices, cloud storage is an essential resource that offers secure and flexible data storage. There is a plethora of different cloud storage software on the marketplace and many users will find themselves utilizing more than one. Consequently, it’s worth using a cloud storage manager that lets you access all your different files in the cloud through a single interface. So we’ll compare two of the leading cloud storage offerings currently available and find out which one offers the best value.
CloudMounter
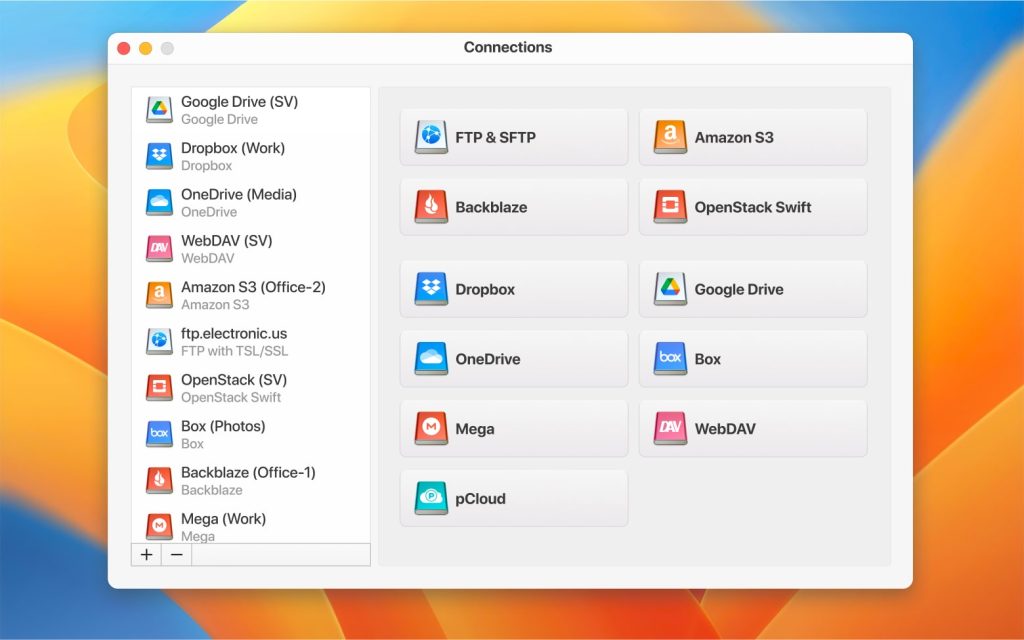
CloudMounter is an innovative RaiDrive alternative for Mac that synchronizes with all the biggest cloud storage providers like Amazon S3, Dropbox, Google Drive, and more. CloudMounter mounts all these services as if they were local disks, letting users navigate cloud storage as a local drive on Windows or macOS. So all you have to do is drag and drop files to seamlessly upload or download them between the cloud and your local device.
If you need to juggle between multiple cloud storage accounts from the same provider, don’t worry: this cloud manager allows you to stay logged into more than one account at the same time, making it perfect for switching files between professional and personal cloud accounts.
Users who struggle with local disk space will also find CloudMounter handy as it lets you edit files on the cloud itself without having to download them to your device. Using CloudMounter doesn’t just save hard drive space — it also reduces the drain on your device’s performance by letting you access all your cloud storage through a single storage tool instead of running programs like Google Drive and Amazon S3 open on your device at the same time.
Security is maintained by end-to-end encryption, and overall CloudMounter’s flexible feature set recommends it to anyone looking for a quality cloud storage manager.
CloudMounter is a great way to have easy and constant access to your cloud storage services from your desktop computer. Its data encryption capabilities make it a secure app, too— Mauricio Preuss, Cloudwards
RaiDrive
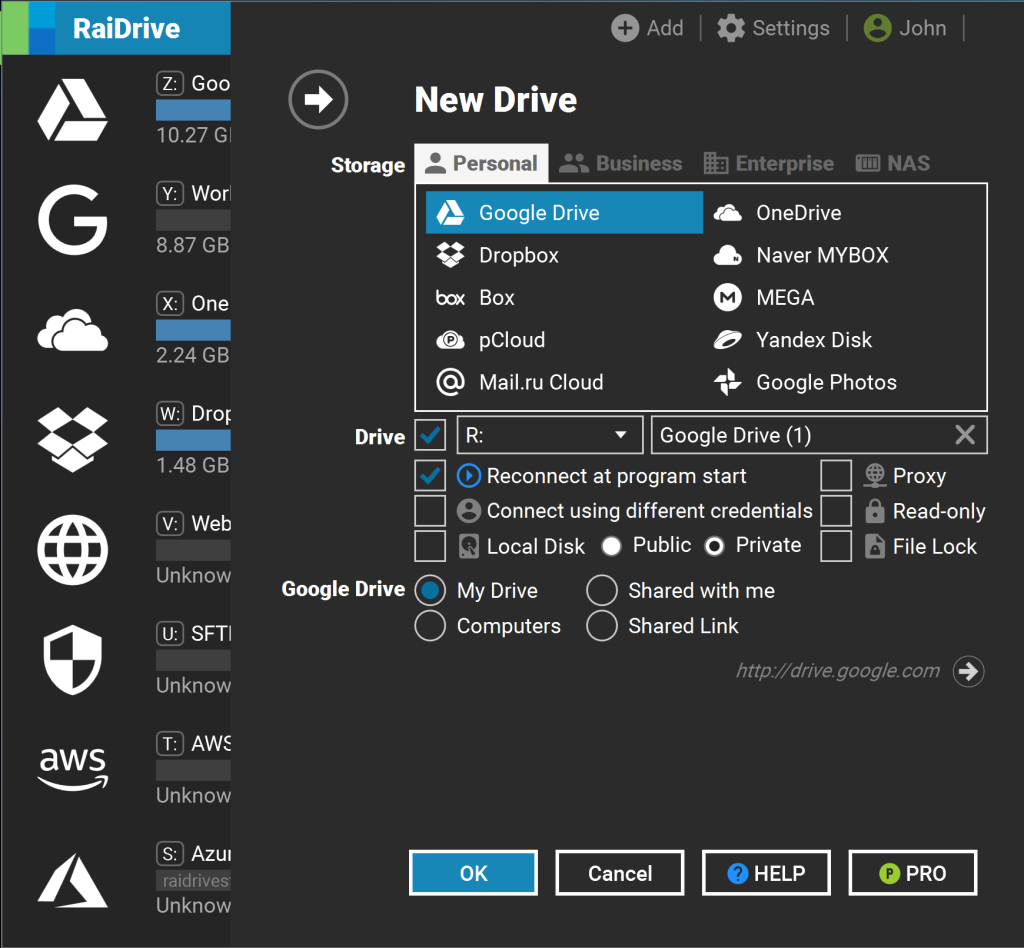
RaiDrive is another cloud storage management app that also lets you mount cloud drives as if they were local storage. It’s compatible with major services like OneDrive, Google Drive, and Amazon Web Services, as well as less mainstream cloud solutions like Backblaze and MEGA.
Perhaps RaiDrive’s best feature is that it lets users play media files in the cloud without having to download them to their devices, so if you have a large library of media stored in the cloud then this will probably come in handy. Elsewhere you have compatibility with WebDAV, SFTP, and FTP file transfer protocols which can help with server management.
RaiDrive does possess a few notable drawbacks, however. Firstly, it’s only available for Windows/Linux, so macOS users will have to find a cloud management app elsewhere. Unfortunately, you also can’t access multiple accounts of the same storage provider at the same time, which lessens the appeal for users with heavyweight file management demands.
There are also a few technical limitations that also hold the program back, such as a lack of command-line control. RaiDrive isn’t the most lightweight app either, and file encryption leaves something to be desired. However, if you want to stream music, movies and TV shows stored in the cloud, RaiDrive might be the service for you.
RaiDrive integrates with the best cloud services such as Dropbox or Box. In addition, it also includes SFTP. This software allows you to mount multiple units in the cloud simultaneously— on G2
CloudMounter VS RaiDrive: Feature Comparison
| # | Features | CloudMounter | RaiDrive |
| 1 | Android Sync | ||
| 2 | Cloud sync | ||
| 3 | Support for Amazon S3 | ||
| 4 | File-sync | ||
| 5 | Support for FTP | ||
| 6 | Dropbox integration | ||
| 7 | Google Drive integration | ||
| 8 | Sync with Google Drive | ||
| 9 | Mount FTP drives | ||
| 10 | Mounting drives | ||
| 11 | Mounting WebDav folders | ||
| 12 | Media Streaming | ||
| 13 | Support for SFTP | ||
| 14 | Support for Dropbox | ||
| 15 | Upload directly to Dropbox | ||
| 16 | Upload directly to Google Drive | ||
| 17 | Support for WebDAV | ||
| 18 | Cloud Storage | ||
| 19 | Encryption | ||
| 20 | Apps with Finder Integration | ||
| 21 | Lightweight | ||
| 22 | Support for MEGA | ||
| 23 | OneDrive integration | ||
| 24 | Simple set up | ||
| 25 | Openstack swift integration | ||
| 26 | Command line interface | ||
| 27 | Sync with Amazon Drive | ||
| 28 | Box.com integration | ||
| 29 | Connect multiple accounts | ||
| 30 | File transfer | ||
| 31 | Mounting local drives |
CloudMounter VS RaiDrive: The Verdict
Both of these cloud management apps have their advantages and disadvantages, as well as similarities. Both these apps let you mount cloud storage as if they were local drives, which provides a seamless experience for managing your files in the cloud. They also offer comprehensive compatibility with all the most popular cloud services along with remote file management that helps free up space on your local hard disk. Both apps also offer compatibility with SFTP, FTP, and WebDAV protocols.
In our opinion, however, CloudMounter offers a stronger service. The simple fact that you can have as many accounts from the same cloud provider open at once as you want gives it a major edge over the competition, especially for users who might need to use cloud storage for professional reasons.
We’re also big fans of the intuitive interface and lightweight design that makes the service easy to navigate. That said, credit has to be given to RaiDrive for its file streaming functions which will be of serious interest to users with big media libraries stored in the cloud. Security is less of a concern with CloudMounter, though, thanks to a cloud encryption function that ensures all your files stay safe from prying eyes, which is another reason why CloudMounter gets the vote.
Popular Articles
Frequently Asked Questions
RaiDrive is only available for Windows/Linux, but CloudMounter is fully compatible with macOS.
CloudMounter is the more secure app, as all transfers feature end-to-end AES-256 security to keep your files protected at all times. Passwords are securely stored in macOS Keychain on Mac devices.
To mount cloud storage as a local drive in CloudMounter, simply launch the program and click the “New Drive” tab and select the cloud service you want to use. Next, enter the login details and password for that account, and continue to access the cloud storage as if it was a local drive in your file explorer.
In RaidDrive, click on the “Add” button and click on the cloud provider, then enter the login information and select any system preferences you want, then click “OK” and the drive will be available to navigate.