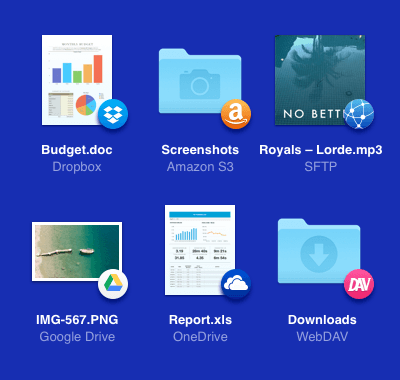
CloudMounter cares about the security of its users that is why it doesn’t save your login credentials to any of your cloud computing services as well as remote servers after logging into them.
This information can be found only in macOS Keychain.
Cloud encryption for Dropbox, Google Drive, OneDrive and others
Make sure that your online documents are totally protected while using CloudMounter. Cloud encryption has never been easier before. Benefit from DropBox, Google Drive, Amazon S3, FTP encryption as well as other major cloud computing services and remote servers. Encrypt data before saving it to the cloud and add extra protection for better control of your online files.
Available for both 
Client-side encryption of all data
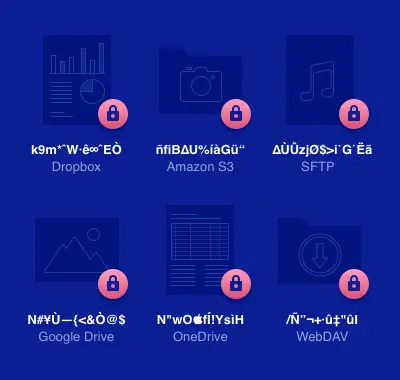
Cloud data encryption is an effective way to improve the security of cloud services that is why CloudMounter perfectly integrates data encryption to make sensitive data inaccessible and protect your cloud and remote servers. Encrypt data before sending it to the cloud and make it accessible only from your own CloudMounter app. We’re talking about file encryption and folder-wide protection as well.
Encryption methods use sophisticated algorithms to hide information protected by the cloud thus making your data unreadable, and only those with the password can access and read it. After all, there’s no such thing as too much cloud security.
CloudMounter

Other app/device

Finder friendly cloud storage encryption app
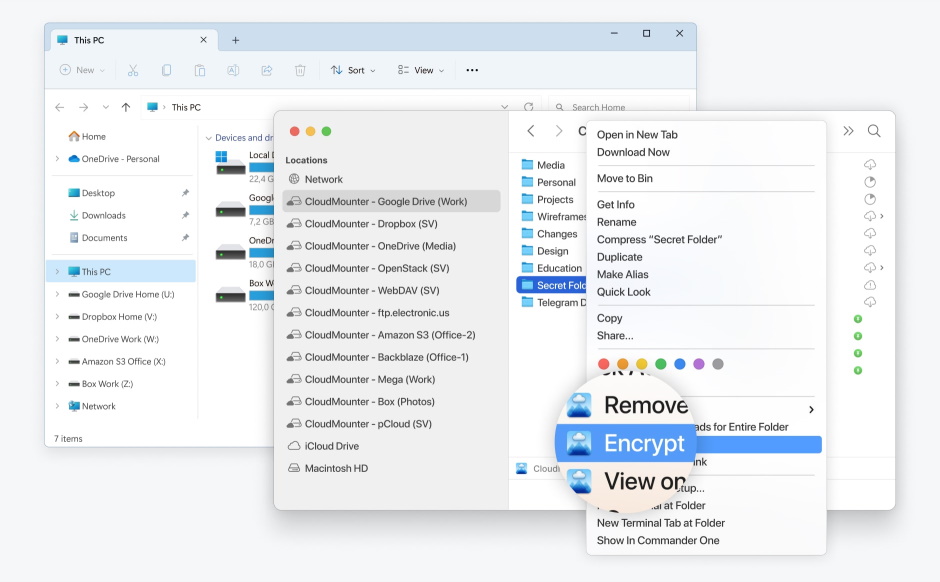
Thanks to smooth and logical integration into Finder the work with online and remote files can be done without even leaving your favorite macOS file manager. Have easy and comprehensive use of the app. Mount as many cloud accounts as you use on your Dropbox, Google Drive, One Drive, Amazon S3 and find them as regular drives in the Finder sidebar. In addition, the app can boast about such feature as encryption in the cloud of your online files that is also a great plus.
Secure storage of credentials
As many accounts as needed
Log into multiple cloud computing accounts as CloudMounter doesn’t limit you in a number of accounts for one cloud service.
Add as many accounts as you have and encrypt cloud data easily to ensure additional protection to your inline files.
Add as many accounts as you have and encrypt cloud data easily to ensure additional protection to your inline files.
Expand your disk space
The easiest way to mount cloud computing services to your Mac and access them all from a single interface without eating up your own disk space or database.
Store your files on the clouds or remote servers and have access on a go. The only thing that is needed is the Internet.
Store your files on the clouds or remote servers and have access on a go. The only thing that is needed is the Internet.
Frequently Asked Questions
Cloud security is a broad term that refers to the use of a collection of technologies, protocols, and best practices to protect files, data and information in a cloud architecture. Cloud security ensures that data stored in the cloud is kept confidential, protected, and compliant.
In general, the fight against vulnerabilities occurs primarily on the server-side: it is the responsibility of the cloud service provider. But clients also have responsibilities, besides choosing a reliable supplier. Customers must use security settings correctly, be able to use services securely, and take care of protecting all end-user devices and networks as well as provide extra precautions such as encrypt files before uploading to cloud.
Of course, it is impossible to vouch for the reliability of all cloud storage - that is why it is so important to approach the choice of service for storing information carefully and scrupulously. However, there the number of trusted cloud computing services is huge: Dropbox, iCloud, Google Drive, pCloud, Mega, OneDrive, Amazon S3, etc. However, additional protection such as using encryption software for cloud storage is always highly welcomed.
The answer to the questions will be yes, cloud computing services can be hacked. The main reason why cloud computing services can be hacked is privacy breaches because of the weak password. That is why it is highly recommended to use a strong password and keep it safe.
There are several cloud security threats, namely:
- System vulnerabilities are a technical issue that the IT department must pay special attention to.
- Errors or negligence on the part of end-device users is a human factor, to fight against which it is necessary to constantly train employees in safety rules.
- Attackers - their capabilities completely depend on the vigilance of users and the security of the cloud system. However, the ability to manipulate people and exploit vulnerabilities gives cybercriminals a significant advantage.
All supported services

CloudMounter
This all-in-one cloud computing encryption software for Mac is fully compatible with macOS 12.4 and later.
Requires 61.08MB of free space, latest version 4.16(2313). Released 4 Dec, 2025.
based on 255 reviews
CloudMounter for Windows
You can now mount your multiple cloud storages as disks on your PC too.